the challenge
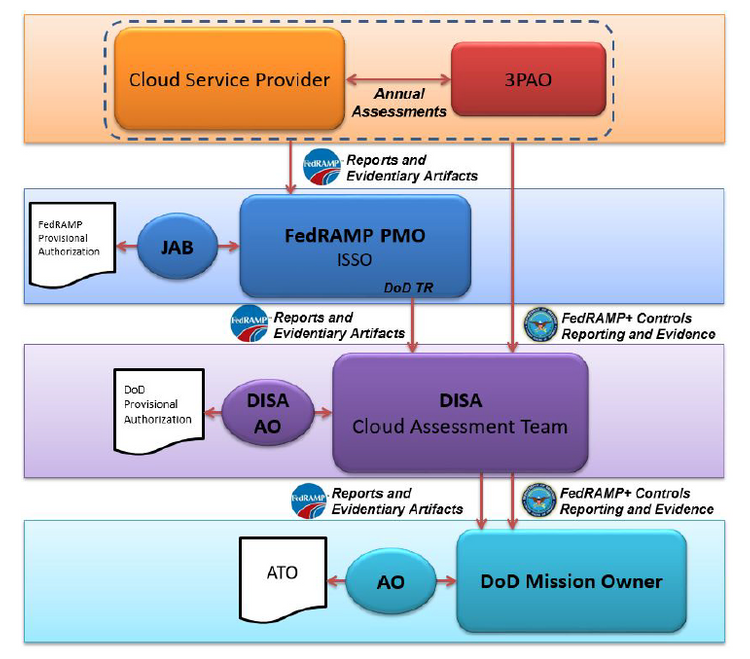
As subject-matter experts and key advisors on the Risk Management Framework (RMF) team, Rotunda Solutions provides critical services to efforts responsible for completing all requirements to authorize an essential cloud platform that provisions and facilitates payment for all DOD customer cloud resources at all classification levels. The accreditation requirements included authoring more than 1500 NIST 800-53 rev. 4 and Cloud Computing Security Requirements Guide (CC SRG) FedRAMP + control implementation statements to validate more than 500 exclusive security controls across nineteen control families by collecting evidence and uploading it into the Enterprise Mission Assurance Support Service (eMASS), a Federal accreditation application. Additionally, the RMF engineer was charged with adjudicating cloud service provider (CSP) control inheritance in accordance with the shared responsibility model, building relationships and collaborating with multiple cloud providers, senior leaders, and stakeholders across disparate Federal agencies and the information technology industry. In our essential role, our engineers write, determine, and oversee the processes, standard operating procedures (SOPs), policies, cloud platform Plan of Action and Milestones (POAM) requirements, and control implementation, while maintaining the accreditation through continuous monitoring and annual security control assessments.
solution provided
The many contributions of the RMF team epitomize an exceptional quality of delivery and a high level of expertise that allows us to consistently deliver innovative value beyond the initial ask. For example, to track the multitude of highly sensitive and mission critical requirements, processes, and products falling under our care (including project delivery, security control implementation, artifact collection, eMASS artifact upload, and other crucial factors) our RMF experts developed a comprehensive Security Requirements Traceability Matrix (SRTM) that not only provided the above capabilities, but also enabled a real-time “one-stop-shop” for senior leadership, stakeholders, and the larger team to collaborate across multiple technologies, tools, enablers, and domains, to include the collaborative environment, STIGs, Non-Classified Internet Protocol Router Network (NIPRNet) and other proprietary machines and capabilities. This is just one example of the propensity of our team to go above and beyond to ensure the success of JEDI.




our approach
The impact of our conscientious, thorough, and holistic approach is evident in our numerous accomplishments and consistent ability help the DoD to overcome obstacles. For example, our RMF engineers used an “out of the box” and systems approach to solve the problem of receiving an elusive Authority to Operate (ATO) for the cloud offering. Instead of following a doctrinal “by the book” solution, the RMF Engineer identified process efficiencies, leveraged expertise and awareness of broader technology resources, briefed stakeholders closely, and ultimately created an actionable project plan to uniquely craft the desired outcome within the constraints of the scenario. Throughout this process, we adhered to our client and problem centered focus, iterating continuously with leadership to refine requirements and ensure understanding, closely tracking project completion, and prioritizing timely delivery of deliverables with an emphasis on operational value.
our results
The RMF engineering team leveraged multiple industry-leading technologies and methods to manage efficient and Agile execution, identifying dependencies and roadblocks early, managing expectations, and empowering the team to offer cogent and operational recommendations. Our RMF team accordingly completed all deliverables and requirements ahead of schedule and maintains a strong reputation with the DoD leadership. The success of these critical activities are essential for the launch of DoD’s JEDI.
- 1500 critical documents authored for JEDI accreditation
- 500 exclusive security controls being continually evaluated
- 19 control families